Necessary Always Active
Necessary cookies are required to enable the basic features of this site, such as providing secure log-in or adjusting your consent preferences. These cookies do not store any personally identifiable data.
|
||||||
|
||||||
|
||||||
|

Ever wondered what lies beyond the internet you browse? It isn’t just what you see on the surface but much more. Are you curious about the dark side of the web? Then this blog answers all your questions about the mysterious Dark Web beyond the Surface Web. Stay tuned since we will be revealing some interesting Dark Web facts that you wouldn’t want to miss out on!
The Dark Web is the side of the internet that is not indexed by standard search engines like Chrome or Bing. It can only be accessed through encrypted web browsers or you can say tools to access the dark web, like The Onion Router (Tor), Freenet, and other such websites. The websites that are accessible through Tor have a “.onion” domain and maintain the user’s anonymity.
While the Dark Web hosts legal and legitimate content, such as privacy-focused forums and whistleblower platforms. But, it is also known for the notorious illegal activities like the black market for drugs, selling of stolen data, and hacking services.
The anonymity surrounding the Dark Web makes it both intriguing and controversial since people argue about its ethical and legal boundaries. Government authorities and cybersecurity professionals continuously observe this untraceable domain to detect and report cyber offenses and cyber attacks.
But advocates defend its usage as a necessity for people living in oppressive countries and legitimate uses of dark web. Whether seen as a threat or a tool for privacy, the Dark Web remains one of the most mysterious areas of the internet.
The internet is divided into three parts: The Surface Web, the Deep Web and the Dark Web. Surface Web refers to the part of the internet that is indexed and could be accessed through browsers like Chrome and Bing. It has a lot of .com, .net and .org sites but only represent 5% of the total internet.
The size of the Deep Web surpasses the Surface Web while remaining secure as an Internet zone. Almost 90% of all the websites are on Deep Web and are majorly used by Government agencies, corporations amongst others. These websites are protected behind the security walls, authentication form and password.
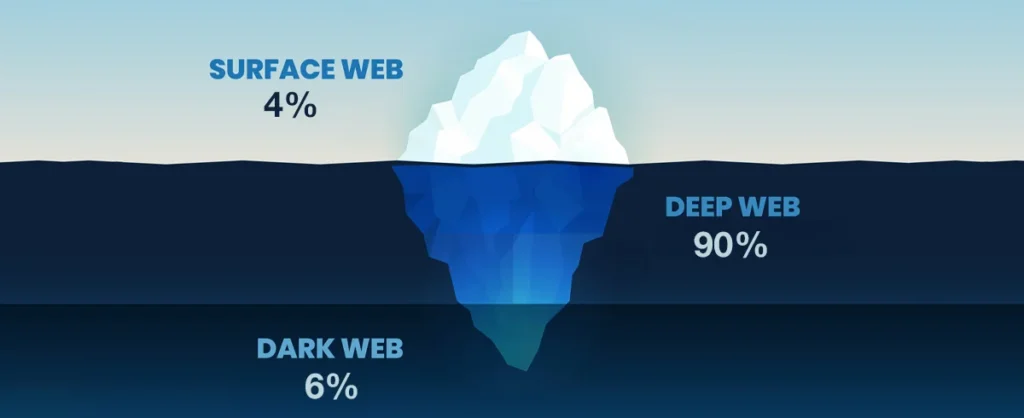
A piece of Deep Web is the Dark Web which can only be accessed through browsers like Tor and Freenet for navigation. Though using the Tor is completely legal and legitimate but there is some content that cannot be accessed as it is a punishable offence.
| Criteria | Surface Web | Deep Web | Dark Web |
|---|---|---|---|
| Definition | Visible and accessible part of the internet | Hidden pages not indexed by search engines | Encrypted part of the web requiring special tools |
| Accessibility | Open to everyone via standard browsers | Requires login or specific permissions | Requires anonymity-focused software like Tor or I2P |
| Search Engine Visibility | Indexed by search engines like Google | Not indexed by public search engines | Not indexed by traditional search engines |
| User Purpose | General browsing and information sharing | Secure data sharing, professional tools | Anonymous communication and activities |
| Security Level | Basic encryption (HTTPS) available | Stronger security measures like two-factor authentication | End-to-end encryption; high risk of illegal activities |
| Anonymity | Minimal or no anonymity | Moderate anonymity with authentication | Complete anonymity through encryption tools |
| Legality | Fully legal | Legal for legitimate purposes | Legal to access but some activities are illegal |
Standard web browsers like Chrome and Firefox do not provide access to the Dark Web. Users access hidden websites securely and anonymously by using specialized browsers such as The Onion Router (Tor) and Invisible Internet Project (I2P). Though, using the Dark Web remains legal in most parts of the world, conducting illegal activities will inevitably result in legal penalties.

The Dark Web serves legitimizing purposes for journalists’ activists and cybersecurity researchers who use it to maintain privacy and conduct research and protected communications. Here are a few browsers through which Dark Web can be easily accessed:
Tor Browser stands as the most popular tool for .onion website access since it protects users with encryption across multiple layers. The Tor application directs users’ internet data through numerous volunteer-operated servers distributed worldwide which protects user activities from tracking.
The software platform operates as a peer-to-peer decentralized system through which users maintain anonymity during communication and file exchanges. Data processed through this network splits into encrypted fragments which get dispersed among different nodes to stop tracking and ensure anonymity.
This networking system delivers private and encrypted communications through an anonymous system for messaging. The fundamental function of I2P that differs from Tor is it builds its own enclosed network that supports users to establish secretive web pages called “eepsites.”
A privacy-focused operating system that routes traffic through Tor for enhanced security. It consists of two virtual machines: one that runs applications and another that connects to the internet via Tor.
GNUnet is a free and open-source framework designed to enable secure, privacy-focused, and decentralized peer-to-peer (P2P) communication. Developed as part of the GNU Project, GNUnet provides a censorship-resistant platform for file sharing, messaging, and various other decentralized applications.
Related Post – Cyber Monday Scams: What Businesses Need to Watch Out for
In short, visiting the dark web itself is not against the law. There are legitimate reasons to explore this part of the internet, and in some cases, it even serves important social and ethical purposes. The dark web offers several distinct advantages to its users, including:
Because of its focus on anonymity, the dark web often attracts individuals who need privacy for valid reasons. These may include whistleblowers, victims of abuse, journalists, and political activists operating under oppressive regimes. However, the same features that make it a refuge for the vulnerable can also make it appealing to those engaging in unlawful activities.
Ultimately, the legality of your actions on the dark web depends on how you use it. Some users navigate it to protect freedom of speech and personal safety, while others may exploit it for purposes that violate the law. To fully understand this, it’s helpful to look at both the tools used to access the dark web and the types of websites found there.
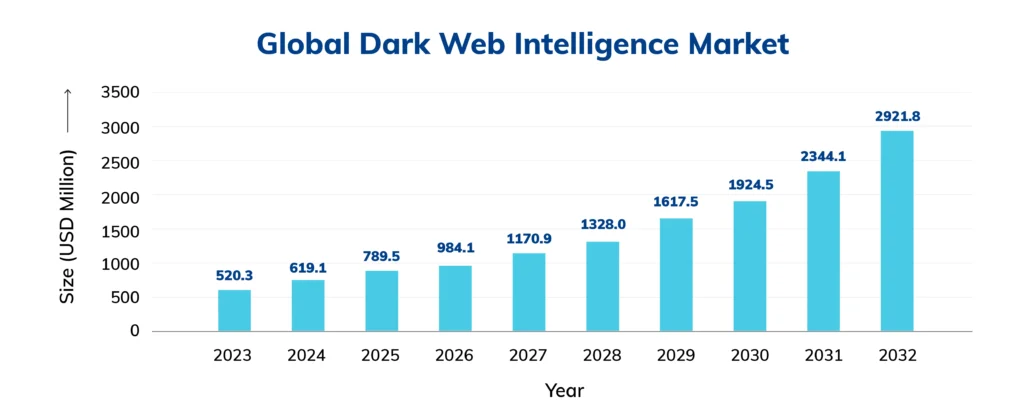
Dark Web is part of a Deep Web which can only be accessed through browsers like Tor or Freenet. According to market.us, the Dark Web Intelligence Market size reached $619.1 million in 2024 and is expected to reach $2921.8 million at a CAGR of 21.8% from 2024-2032.
The dark web intelligence market experiences a dynamic increase in cybercriminal operations. 4iQ reported that stolen account credentials on the dark web experienced an 82% increase in 2022 to reach 15 billion. Identity theft cases lead the dark web monitoring activities at 65% while credit card fraud follows closely behind at 15% and the number of card dumps exceeds 192 million according to Sixgill’s reports. Chainalysis researchx` Anatomy reveals dark web cryptocurrency activity almost doubled between 2020 and reached $25 billion in 2022 thus underscoring the necessity for advanced tracking systems.
The Dark Web is infamous for its illegal activities like black markets and cybercrimes along with illicit transactions but simultaneously supports legitimate applications to protect privacy help activists communicate safely and allow access to restricted content in closed territories. Here are a few legal uses of the Dark web:
One of the major advantages of the Dark Web is the maintenance of “Privacy and anonymity”. Journalists, activists and others use the Dark Web to communicate safely and anonymously to avoid censorship. Platforms like SecureDrop provide a safe space to communicate and share information anonymously.
There are a lot of websites and information that cannot be accessed through the Surface Web. The Dark Web helps in bypassing restrictions and accessing blocked websites, social media and news sources. People living in countries with internet censorship can access news through these websites as they are untraceable due to high security. Activists and journalists can also utilize the Dark Web to gather sensitive data which cannot be accessed through surface media or present their unbiased opinion through these platforms.
Governments around the globe hire ethical hackers to get an insight into various information. Access to the Dark Web can help in providing a lot of leaked data that helps in the prevention of cyber threats, protecting a lot of individuals and organizations.
The UK and the US have strong legal frameworks regarding data breaches because data leaks constitute severe incidents. GDPR violations in the UK can lead to maximum fines that reach either £17.5 million or 4% of the organization’s global annual turnover.
Also, global data privacy highlights the contrasting approaches of the United States, the European Union, and rapidly digitizing economies such as India in controlling and protecting personal data.
The U.S. Data Breach Notification Laws mandate rapid breach reporting from companies while HIPAA and similar regulations enforce healthcare organizations to pay fines reaching up to $1.5 million for each recorded violation.
Researchers and law enforcement professionals use the Dark Web to understand crime patterns and illegal activities by notorious groups to prevent these crimes from happening. It could also be used to gather information about criminals that cannot be accessed easily through indexed websites.
Cryptocurrency is used as a transactional unit on the Dark Web. However, there are a lot of forums that decentralize finance legally by discussing blockchain and other forms of investments. Decentralization helps users gain more knowledge about the working of block chain across various industries and strengthen their investment game.
Although the Dark Web enables absolute privacy along with forbidden content access it functions as a dangerous domain where illegal operations create ethical dilemmas and legal complications. Users are increasing their investments in Dark Web Intelligence services because it plays a key role in criminal investigation while businesses and academics both need insight into digital threats.
While the Dark Web hosts illegal activities, it also supports legitimate uses like protecting free speech and aiding cybersecurity. A person must exercise caution while accessing the Dark Web, while being mindful of legal obligations and possessing an ethical perspective. The debate about how best to balance technology regulation against anonymous benefits will transform as science advances.
Sign up to receive our newsletter featuring the latest tech trends, in-depth articles, and exclusive insights. Stay ahead of the curve!